
Complying with the CRA (Cyber Resilience Act)
Cybersecurity is a mandatory cybersecurity requirement for products with digital elements. Enterprise security is now both a product design and post-deployment priority.
Cyber resilience is now a legal product requirement in the EU. Learn how the Cyber Resilience Act impacts digital products, from security by design and risk controls to SBOMs, incident reporting, and the 2026–2027 enforcement timeline.
CRA Compliance
The EU Cyber Resilience Act (CRA) establishes a unified cybersecurity framework for digital products placed on or sold within the European Union. It ensures products with digital elements are secure by design, by default, and throughout their development lifecycle.
CRA compliance is especially critical for AI products. Whether your AI system is embedded in hardware, delivered as standalone software, or integrated into a larger digital service, the CRA applies if it has network connectivity or processes data.
CRA is also relevant to IoT products. As the CRA sets mandatory cybersecurity requirements for any product with digital elements, this includes most IoT devices such as hardware, software and related connected services. Because many IoT devices are widely deployed, hard to update, and connected to critical systems, the CRA is yet another EU regulation that these products must meet.
CRA shifts cybersecurity from internal practices to a legal obligation requiring manufacturers and vendors to proactively manage cyber risks from development through post-market operations.
Key Pillars of CRA Compliance
CRA compliance is built around several foundational pillars.
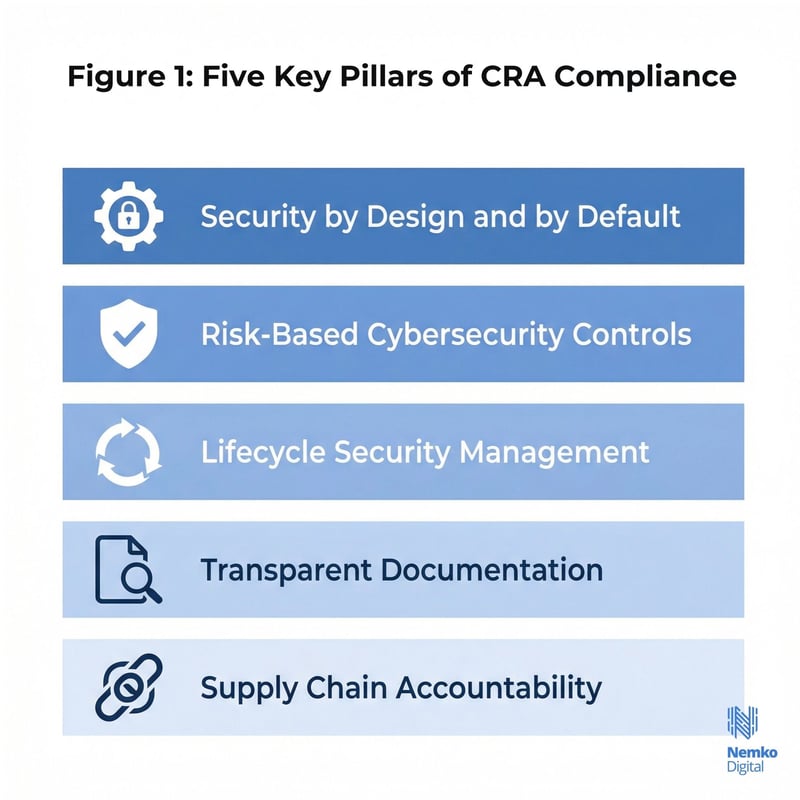
Security by Design and by Default
Products must be designed with cybersecurity controls embedded from the earliest development stages. It cannot be added at a later stage as patches or workarounds.
Risk-Based Cybersecurity Controls
Security measures must reflect the level of risk posed by the product, including its intended use, deployment environment, and potential impact if compromised.
Lifecycle Security Management
Cybersecurity responsibilities extend beyond product launch, covering updates, vulnerability management, and long-term maintenance, such as customer support/warranty.
Transparent Documentation
Manufacturers must clearly document security features, limitations, and usage requirements to support safe deployment and regulatory oversight.
Supply Chain Accountability
Third-party components, open-source libraries, or AI system dependencies must be assessed and managed as part of overall product security.
Core Obligations for Companies
Under the CRA, companies distributing products must build security and compliance into product development and maintenance post launch.
Below is a table outlining CRA Compliance pillars as well as supporting evidence that can be submitted to satisfy each compliance section.
| Scoping & Applicability | Inventory of products with digital elements; classification documentation | Applicability assessment report |
|---|---|---|
| Risk Assessment | Cybersecurity risk assessment reports, threat models | Risk analysis testing and threat modeling |
| Security by Design & Default | Secure development policies across product lifecycle, architectural security documentation | Secure code reviews and design validation |
| Vulnerability Management | Vulnerability handling procedures; AI Software Bill of Materials (AISBOM) | Vulnerability scanning & lifecycle testing |
| Incident Reporting Preparedness | Incident response plans; reporting checklists | Tabletop and live incident response exercises |
| Technical File & Conformity Documentation | Technical file including SBOMs, build logs, CE declaration of conformity | Conformity assessment (self or third-party) |
| Product Testing & Certification | Test report summaries; certification evidence | Security testing (automated & manual); external certification if required |
| Post-Market Surveillance & Updates | Patch, update and monitoring logs; customer support change records | Regression testing for updates; ongoing compliance checks |
The obligations above apply to manufacturers, importers, and distributors, depending on their supply chain role in bringing the product to market.
Timeline of CRA Regulation & Enforcement

The Cyber Resilience Act was approved in 2024 but will not come in full enforcement until December 2027. This gives enterprises a grace period timeline to prepare for compliance.
- 2024 – CRA formally adopted at the EU level
- 2025 – Regulation enters into force; transition period begins
- September 11, 2026 – Vulnerability handling, incident reporting, and conformity preparation ramps up. Manufacturers will be required to notify the European Union Agency for Cybersecurity (ENISA) and Member State authority of actively exploited vulnerabilities and severe incidents affecting in-scope products. This notification must be made without undue delay, and in any event within 24 hours of the manufacturer becoming aware of the vulnerability or incident.
- December 11, 2027 – Full CRA compliance becomes mandatory for products placed on the EU market.
The 2024 to 2027 transition window gives product teams time to align development, security, and compliance processes.
Summary
The Cyber Resilience Act represents a major change in how cybersecurity is regulated for products with digital elements in the EU. Compliance is no longer optional or an afterthought. It is a core product requirement, meaning cybersecurity must be built into product design from the start.
For companies, meeting CRA obligations means designing products with security in mind, managing risks on an ongoing basis, and providing documentation proving accountability and transparency. By meeting compliance, you gain trust with customers, safeguard sensitive data, and protect the company's reputation. Preparing early not only reduces regulatory risk, but also builds stronger, more trusted products and positions products for long-term adoption in the EU market.
Dive further in the AI regulatory landscape
Nemko Digital helps you navigate the regulatory landscape with ease. Contact us to learn how.




